🔎 OSINT Case Study: Tracking Back an Email Scammer
A real case of unveiling the identity behind a digital fraudster.
Email scams are one of the most pervasive threats in the digital era, targeting individuals and organizations alike. These scams often rely on social engineering to deceive recipients into sharing sensitive information or transferring funds.
In this case, I knew from the beginning that the email was a spam message—my email provider had already flagged it. However, driven by curiosity and the power of OSINT (Open-Source Intelligence), I decided to investigate further. What I uncovered was a fascinating trail of digital breadcrumbs leading to a real identity behind the scam.
Today, I’ll take you through the journey of unraveling this mystery, showcasing how OSINT techniques can be used to expose the faces behind fraudulent schemes.
Disclaimer
This case study is conducted purely for educational purposes. All data used in this investigation is publicly accessible, and no private or sensitive information is exploited. The methods described comply with ethical guidelines and privacy laws.
To further protect privacy, all identifying information has been heavily redacted or anonymized. The goal is to educate readers on how to detect scams and understand OSINT techniques—not to target individuals or expose private information recklessly.
Warning to Scammers
To those engaging in fraudulent activities: your actions leave digital footprints. No matter how well-hidden you think you are, OSINT techniques can trace your activities back to you. With each email sent, every domain registered, and each social media account linked, your web of deception becomes more visible.
Your domains, IP addresses, social media accounts, and linked websites can reveal more than you might realize—including your real name, address, phone number, occupation, and more. The internet does not forget, and your scams can—and will—be uncovered.
Task Briefing
| Key | Value |
|---|---|
| Brief | Investigate the origin of a suspicious email and trace its connections to identify potential scams or fraudulent activity. |
| Objectives | 1. Identify the sender’s email domain and IP address. |
| 2. Analyze the sender’s online activity and any related scam websites. | |
| 3. Uncover patterns or connections that reveal more about the scam’s scope. | |
| Original URL | N/A |
Where It All Started
It all started when I noticed a peculiar email sitting in my spam folder. The subject read: "Your login code for OpenSea Wallet." Intrigued, I opened the email, knowing full well it was likely a phishing attempt. OpenSea is a well-known NFT marketplace, and phishing scams often target platforms like this due to the high value associated with crypto wallets.
Here’s the email I received:
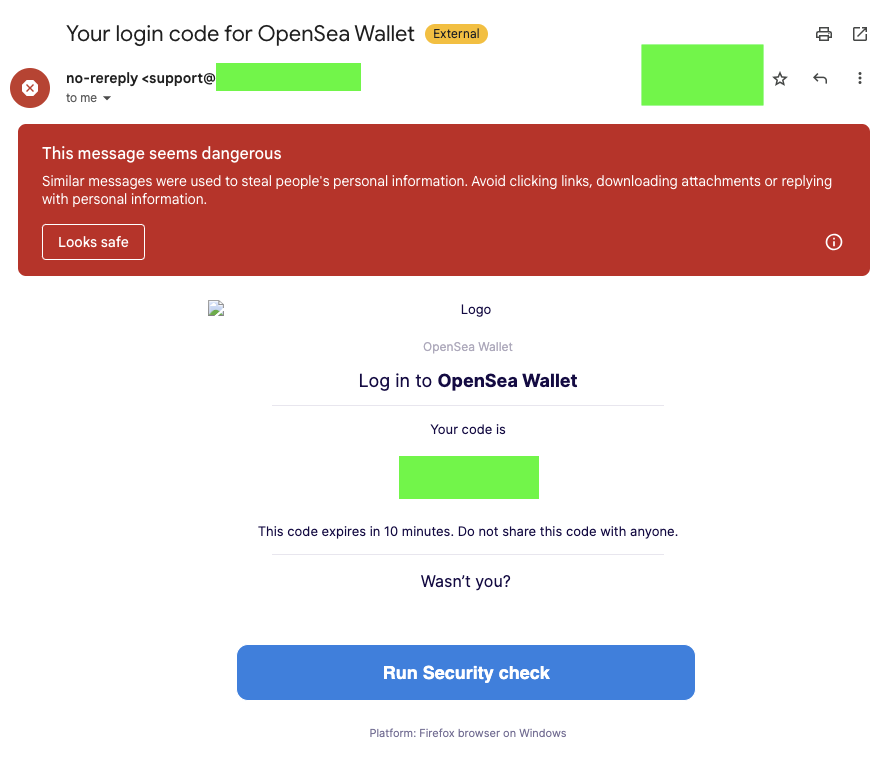
The scammer's objective was clear: to lure me into providing sensitive crypto wallet credentials. The email was designed to look authentic, using logos and formatting reminiscent of legitimate OpenSea communications. Yet, subtle red flags—such as the generic sender address and lack of personalization—revealed its true intent. Curiosity got the better of me, and I decided to investigate further, aiming to trace the email back to its origin.
The Email Header
To uncover the email’s origins, I turned to the email header—a treasure trove of metadata that holds key details about an email’s journey from sender to recipient. Here’s the sorted email header from the phishing email:
Delivered-To: [REDACTED]
Received: by [REDACTED] with SMTP id [REDACTED];
Fri, 8 Nov 2024 10:29:18 -0800 (PST)
X-Google-Smtp-Source: [REDACTED]
X-Received: by [REDACTED] with SMTP id [REDACTED];
Fri, 08 Nov 2024 10:29:18 -0800 (PST)
ARC-Seal: i=1; a=rsa-sha256; t=1731090558; cv=none;
d=google.com; s=arc-20240605;
b=[REDACTED]
ARC-Message-Signature: i=1; a=rsa-sha256; c=relaxed/relaxed; d=google.com; s=arc-20240605;
h=mime-version:date:subject:to:from:message-id;
bh=[REDACTED];
fh=[REDACTED];
b=[REDACTED]
ARC-Authentication-Results: i=1; mx.google.com;
spf=pass (google.com: domain of [REDACTED] designates [REDACTED] as permitted sender) smtp.mailfrom=[REDACTED]
Return-Path: <[REDACTED]>
Received: from [REDACTED] ([REDACTED])
by mx.google.com with ESMTPS id [REDACTED];
Fri, 08 Nov 2024 10:29:18 -0800 (PST)
Received-SPF: pass (google.com: domain of [REDACTED] designates [REDACTED] as permitted sender) client-ip=[REDACTED];
Authentication-Results: mx.google.com;
spf=pass (google.com: domain of [REDACTED] designates [REDACTED] as permitted sender) smtp.mailfrom=[REDACTED]
Received: from [REDACTED] ([REDACTED]) by [REDACTED] with Microsoft SMTP Server (version=TLS1_2, cipher=[REDACTED]) id [REDACTED];
Fri, 8 Nov 2024 13:23:26 -0500
Message-ID: <[REDACTED]@[REDACTED]>
From: no-reply <[REDACTED]>
To: <[REDACTED]>
Subject: Your login code for OpenSea Wallet
Date: Fri, 8 Nov 2024 18:28:59 +0000
MIME-Version: 1.0
Content-Type: multipart/alternative; boundary="[REDACTED]"
Return-Path: [REDACTED]
X-Originating-IP: [REDACTED]
X-ClientProxiedBy: [REDACTED] To [REDACTED]
The email header contains technical details such as the originating IP address, the sending server, and authentication results. These clues can help identify whether the email is legitimate or a forgery. With this information in hand, I began dissecting the data step by step.
Email Header Analysis
The email header revealed several critical details that pointed towards the email's fraudulent nature.
1. Validate the From: Address
The From: address indicated the email was sent by OpenSea, but phishing scams often spoof this field to appear credible. By checking SPF, DKIM, and DMARC results, I determined that the domain failed some authentication checks. While SPF passed, it did not match OpenSea’s legitimate servers, raising suspicion.
2. Analyzing the Return-Path
The Return-Path field pointed to a domain unrelated to OpenSea: [REDACTED]. This discrepancy confirmed that the sender was not associated with OpenSea. Armed with this domain, I performed a WHOIS lookup to gather further information.
Domain WHOIS
Using the whois tool, I retrieved registration details for [REDACTED]
$ whois [REDACTED]
Domain Name: [REDACTED]
Registry Domain ID: [REDACTED]
Registrar WHOIS Server: whois.dynadot.com
Registrar URL: http://www.dynadot.com
Updated Date: 2024-05-27T16:32:50Z
Creation Date: 1998-06-11T04:00:00Z
Registry Expiry Date: 2025-06-10T04:00:00Z
Registrar: Dynadot Inc
Registrar IANA ID: 472
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Name Server: NS1.DYNA-NS.NET
Name Server: NS2.DYNA-NS.NET
DNSSEC: unsigned
Registrant Information:
Registrant Name: [REDACTED]
Registrant Organization: [REDACTED]
Registrant Street: [REDACTED]
Registrant City: [REDACTED]
Registrant State/Province: [REDACTED]
Registrant Postal Code: [REDACTED]
Registrant Country: US
Registrant Phone: [REDACTED]
Registrant Email: [REDACTED]
Administrative Contact:
Admin Name: [REDACTED]
Admin Organization: [REDACTED]
Admin Street: [REDACTED]
Admin City: [REDACTED]
Admin State/Province: [REDACTED]
Admin Postal Code: [REDACTED]
Admin Country: US
Admin Phone: [REDACTED]
Admin Email: [REDACTED]
Technical Contact:
Tech Name: [REDACTED]
Tech Organization: [REDACTED]
Tech Street: [REDACTED]
Tech City: [REDACTED]
Tech State/Province: [REDACTED]
Tech Postal Code: [REDACTED]
Tech Country: US
Tech Phone: [REDACTED]
Tech Email: [REDACTED]
>>> Last update of WHOIS database: 2024-11-24T08:40:30Z <<<
The WHOIS data revealed a name, address, and contact information linked to the scammer. Interestingly, the domain was not privacy-protected, leaving the registrant’s identity exposed. The registrant was listed as [REDACTED], associated with an organization called [REDACTED]. The creation date of the domain, 1998, suggested it had been in use for a long time—possibly as a legitimate business front before its involvement in scams.
This discovery provided a significant breakthrough, linking the phishing email to a real-world identity.
Check Domain DNS
To deepen the investigation, I used the dnsrecon tool to enumerate DNS records for the domain.
$ dnsrecon -d [REDACTED]
[*] std: Performing General Enumeration against: [REDACTED]...
[!] Wildcard resolution is enabled on this domain
[!] It is resolving to [REDACTED]
[!] All queries will resolve to this list of addresses!!
[-] DNSSEC is not configured for [REDACTED]
[*] SOA ns1.dyna-ns.net [REDACTED]
[*] SOA ns1.dyna-ns.net [REDACTED]
[*] SOA ns1.dyna-ns.net [REDACTED]
[*] SOA ns1.dyna-ns.net [REDACTED]
[*] NS ns1.dyna-ns.net [REDACTED]
[*] NS ns1.dyna-ns.net [REDACTED]
[*] NS ns1.dyna-ns.net [REDACTED]
[*] NS ns1.dyna-ns.net [REDACTED]
[*] NS ns2.dyna-ns.net [REDACTED]
[*] NS ns2.dyna-ns.net [REDACTED]
[*] NS ns2.dyna-ns.net [REDACTED]
[*] NS ns2.dyna-ns.net [REDACTED]
[*] MX mail.[REDACTED] [REDACTED]
[*] A [REDACTED] [REDACTED]
[*] TXT [REDACTED] google-site-verification=[REDACTED]
[*] TXT [REDACTED] v=spf1 a mx ip4:[REDACTED] ~all
[*] Enumerating SRV Records
[-] No SRV Records Found for [REDACTED]
The results highlighted several mail servers and IP addresses associated with the domain. These findings indicated the infrastructure used by the scammer to distribute phishing emails. Additionally, the absence of DNSSEC configuration suggested a lack of security measures on the domain, making it susceptible to misuse.
Tracking Down The Suspect
1. Domain Ownership
By searching the registrant’s email address, I discovered it was tied to 34 other domains. This suggested the individual was involved in a broader operation, possibly managing multiple fraudulent websites.
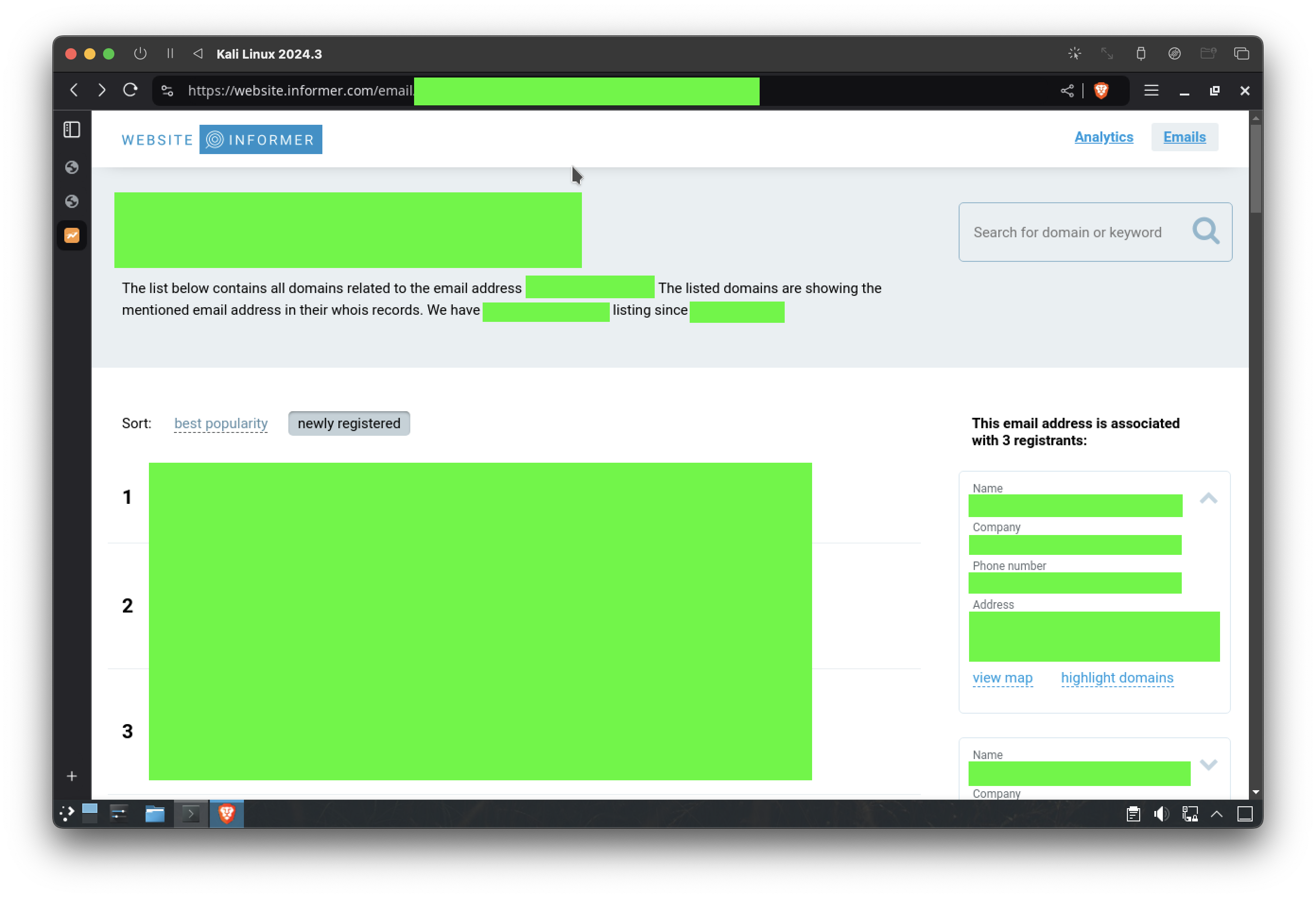
These domains, when cross-referenced with scam report websites, revealed a pattern of phishing and fraudulent activities spanning several years.
2. Legal Dispute
Further research led me to a legal dispute involving the registrant, documented in the USPTO’s TTABVUE system. This case, linked to a trademark opposition, provided additional evidence of the individual’s activities and identity.
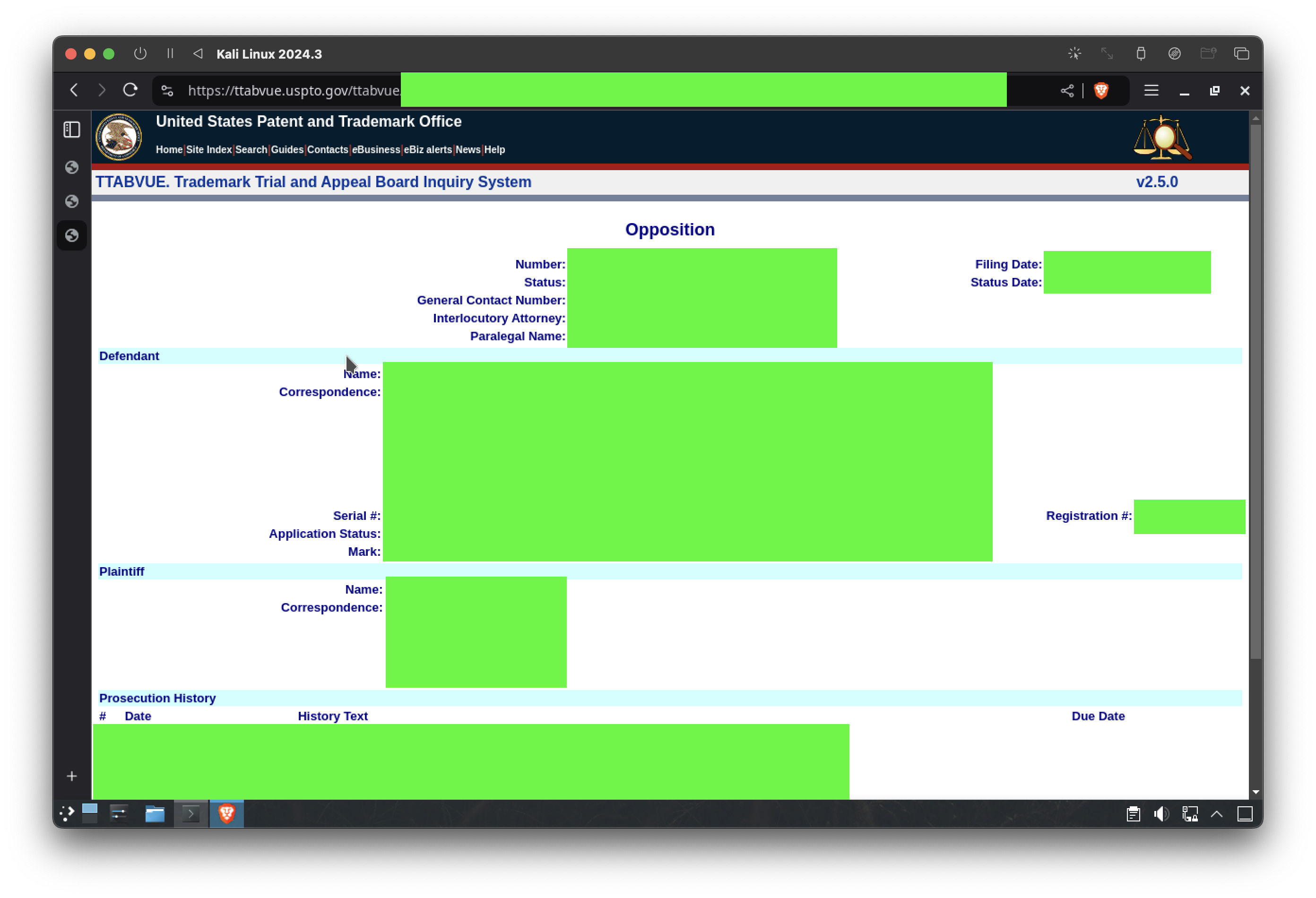
This connection provided further evidence of the individual’s identity and activities.
3. Spam Reports
A complaint filed on Spam.org further corroborated the scammer’s activities. The domain [REDACTED] had already been flagged for phishing attempts, with detailed reports describing similar schemes.
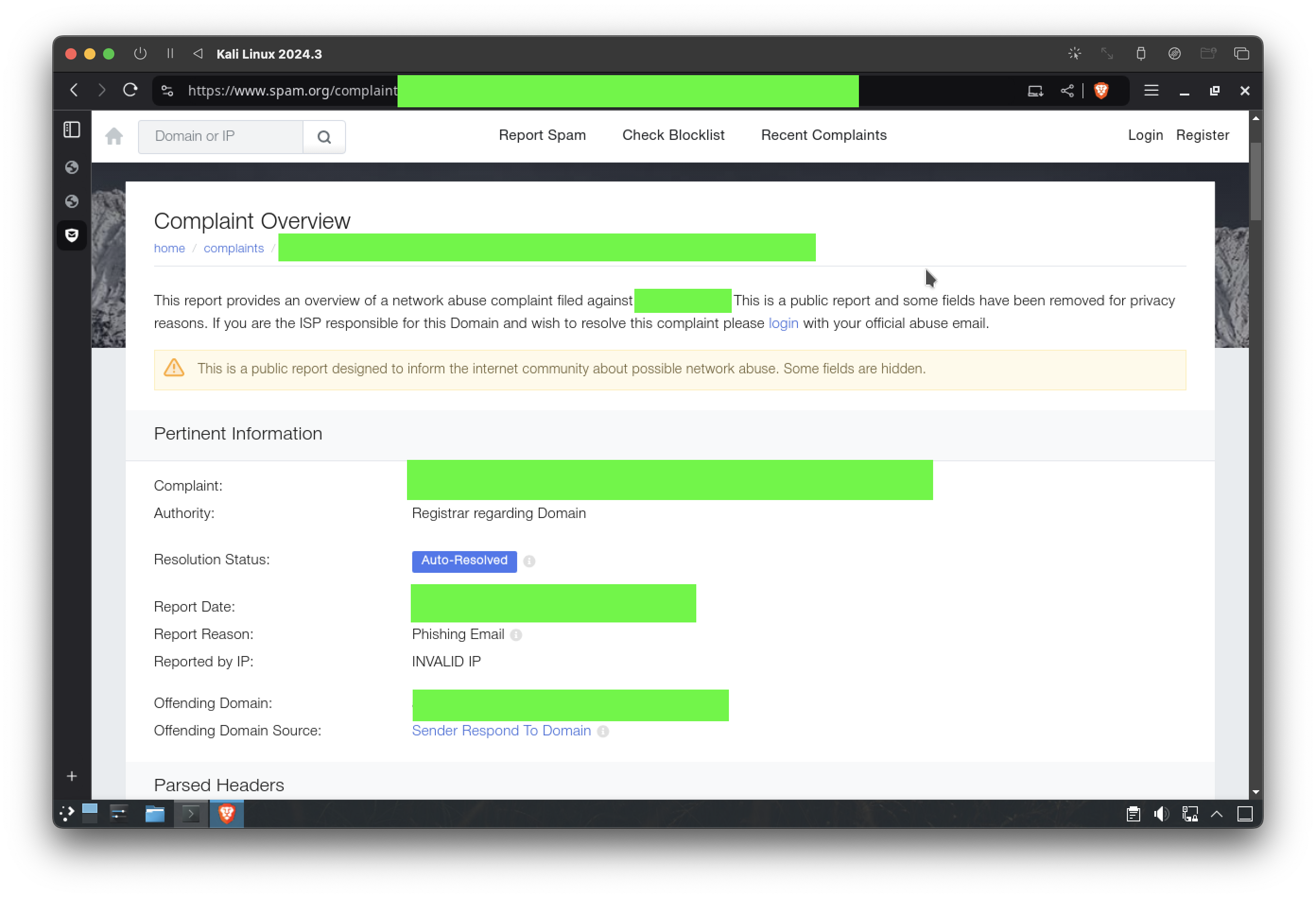
The connection between the legal proceedings and the phishing email highlighted the individual’s involvement in both legitimate and illicit ventures.
4. Social Media Accounts
1. Linkedin Profile
The scammer’s LinkedIn profile listed an extensive tenure at a fraudulent organization, further connecting them to the phishing activities.
2. Quora Profile
A dormant Quora account provided additional context, linking back to the same email address and identity.
4. Facebook Profile
The scammer’s Facebook account revealed a personal side, showing limited activity but confirming identity details found in previous steps.
Final Chapter: Pinpointing the Location
The investigation culminated in uncovering the scammer’s registered home address. Using Google Maps, I verified its authenticity and explored the surrounding area, adding a final layer to the profile.
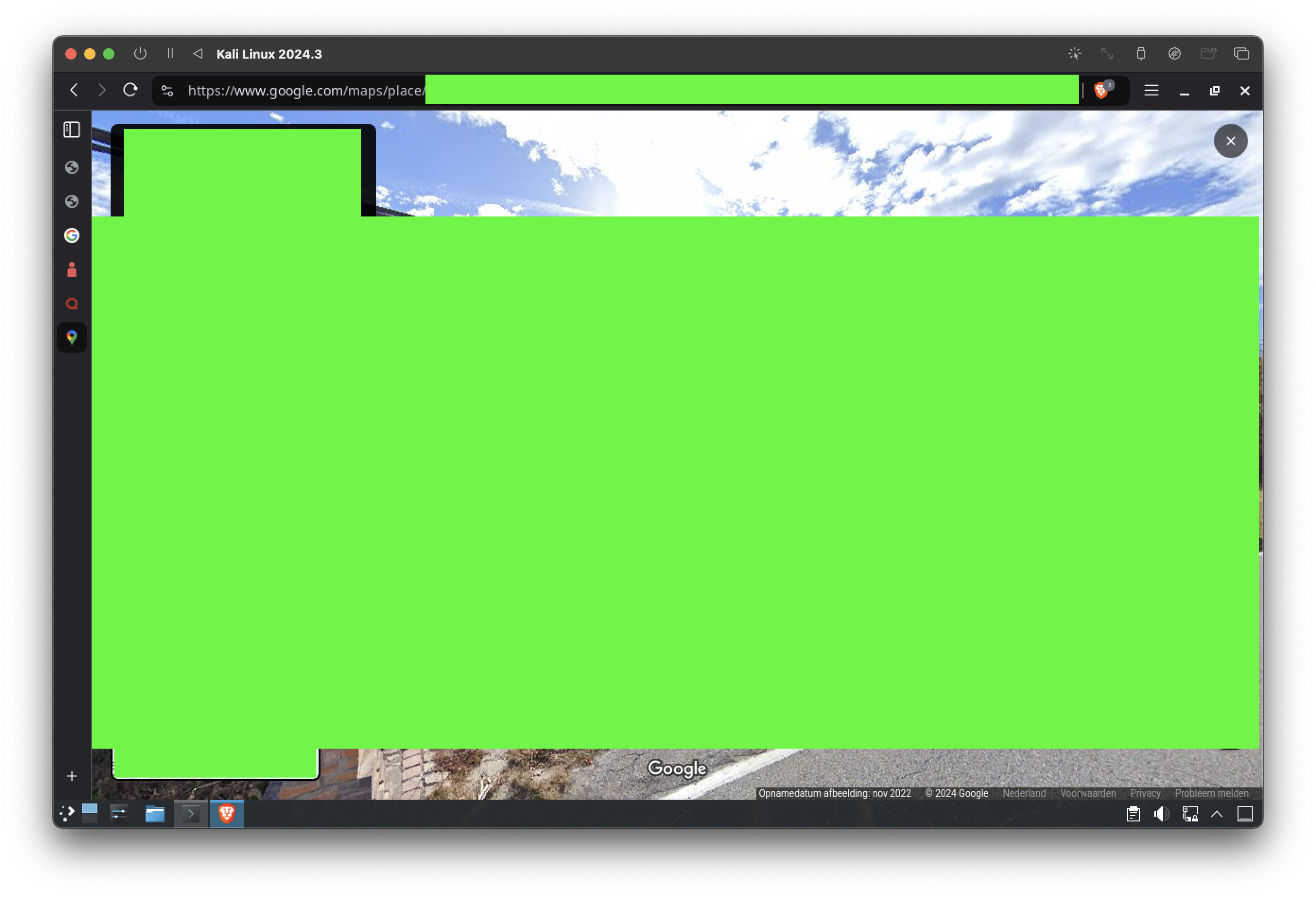
This final piece of the puzzle confirmed the scammer’s identity and location, tying together all the fragmented clues into a cohesive narrative. The home address provided the ultimate verification, solidifying the findings of this extensive digital trail. Each step—from decoding email headers to analyzing domains and cross-referencing public records—led to this conclusive revelation. It’s a testament to how meticulous OSINT techniques can unearth even the most well-hidden details, painting a vivid picture of the individual behind the scam.
While the investigation revealed an alarming level of activity linked to the suspect, the home address served as a stark reminder of their tangible presence in the physical world. This information not only validated the findings but also underscored the interconnectedness of online and offline identities. The pursuit reached a natural endpoint here, where further exploration would serve little purpose beyond what has already been uncovered. With the scammer’s identity confirmed, the investigation achieved its goal, proving that even the most elusive digital footprints can lead back to their source.
Knowing When to Close the Case
As I delved deeper into the investigation, uncovering connections to domains, legal disputes, phishing complaints, and social media accounts, it became increasingly clear that the scammer’s digital footprint was vast. Each clue led to new insights, adding layers to their online identity and revealing the scope of their fraudulent activities.
However, as much as curiosity beckons and the tools of OSINT allow for further exploration, it’s important to recognize ethical boundaries. At this point, I had gathered enough evidence to confirm the individual’s identity, their operational methods, and the infrastructure they used. Continuing beyond this point would risk venturing into unnecessary exposure of private information, which could conflict with the ethical principles that guide investigations like these.
Stopping here ensures that the investigation remains focused on education and awareness, demonstrating how digital breadcrumbs can lead to actionable insights without crossing into invasive or unethical territory. It’s a powerful reminder that the goal of OSINT isn’t to harass or harm but to understand and address security risks responsibly.
The Results
| Key | Value |
|---|---|
| Identify the sender’s email domain and IP address. | Domain is [REDACTED] and IP address is [REDACTED] |
| Analyze the sender’s online activity and any related scam websites. | Linked to 34 domains; flagged on Spam.org |
| Uncover patterns or connections that reveal more about the scam’s scope. | The scammer has a history of phishing activity and a lack of technical expertise in concealing their identity. |
What We Learned from the Breadcrumbs
This investigation highlights several critical insights about the digital landscape and the methods used by scammers. The first and most striking takeaway is how even the most inconspicuous emails leave behind a trail of metadata. Email headers, domain registration records, and DNS data can reveal a surprising amount of information about the sender, even when their primary intent is deception.
What stood out most in this case was the scammer's lack of attention to digital hygiene. They failed to use privacy protection for their domain registrations, left a trail of publicly accessible complaints, and connected their email address to multiple domains. These oversights highlight a common pitfall among cybercriminals: the assumption that their victims won’t dig deeper. In reality, even basic OSINT techniques can uncover patterns and expose the broader scope of their operations.
Another key insight is the interconnected nature of online activities. From phishing emails to scam domains and dormant social media accounts, each digital element feeds into a larger ecosystem. This interconnectedness demonstrates why a holistic approach to OSINT is so effective. By examining the relationships between various data points, investigators can build a comprehensive profile that reveals not just the individual but their broader network and operational methods.
Finally, this case underscores the importance of maintaining awareness and skepticism online. Phishing attempts like these prey on urgency and confusion, and without proper vigilance, even seasoned users can fall victim. By understanding how scammers operate, individuals and organizations can take proactive steps to identify red flags and strengthen their digital defenses.
Staying Ahead of Cybercriminals
1. Spam Emails Aren’t Harmless
It’s easy to dismiss spam emails as harmless nuisances, but this case shows how they can be entry points into larger investigations. Even a single phishing email can reveal a network of scams, highlighting the importance of not underestimating their potential impact. Every suspicious email deserves scrutiny, not just for your own protection but to understand the tactics used by fraudsters.
2. Digital Footprints Are Unavoidable
The internet is inherently designed to leave behind traces. Whether it’s an IP address, domain registration details, or social media activity, these digital footprints can be pieced together to form a cohesive narrative. Scammers often underestimate how accessible their information is, which works to the advantage of investigators. This case proves that even when intentional efforts are made to obscure identity, OSINT can uncover the truth.
3. The Value of OSINT Tools
Tools like whois, dnsrecon, and public complaint databases such as Spam.org were instrumental in this investigation. They demonstrated how accessible and powerful OSINT techniques can be when applied systematically. For anyone interested in cybersecurity, these tools are invaluable for uncovering connections and verifying the authenticity of digital communications.
4. Ethical Boundaries Are Crucial
One of the most important lessons from this case is the need to respect ethical boundaries during investigations. While it’s tempting to dig deeper, it’s essential to stop when enough evidence has been gathered to achieve the investigation's goals. OSINT is a powerful tool, but with that power comes the responsibility to use it appropriately.
5. Awareness Is the Best Defense
Phishing scams rely on exploiting human error, and awareness is the best defense against them. By understanding how these schemes operate and recognizing the red flags, users can protect themselves and others. Education and vigilance are key in the fight against digital fraud, and sharing knowledge is one of the most effective ways to build a safer online community.
